Russian television anchor Pavel Lobkov was in the studio getting ready for his show when jarring news flashed across his phone: Some of his most intimate messages had just been published to the web.

Days earlier, the veteran journalist had come out live on air as HIV-positive, a taboo-breaking revelation that drew responses from hundreds of Russians fighting their own lonely struggles with the virus. Now he’d been hacked.
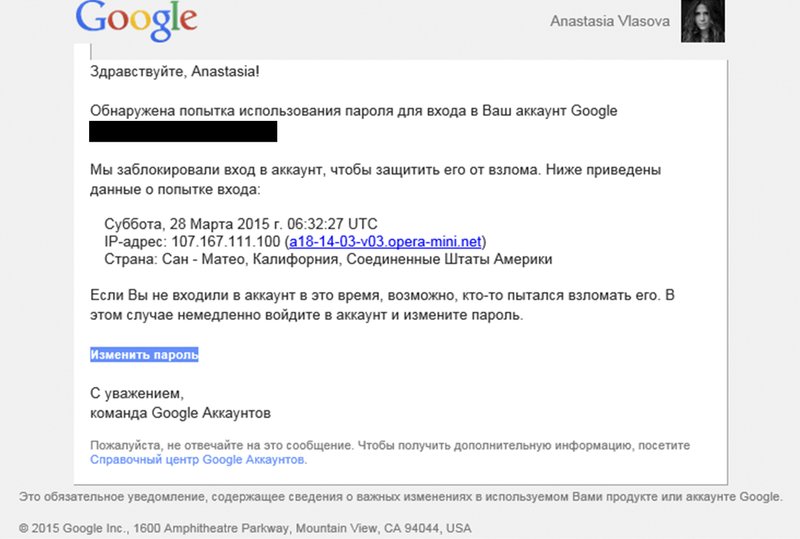
“These were very personal messages,” Lobkov said in a recent interview, describing a frantic call to his lawyer in an abortive effort to stop the spread of nearly 300 pages of Facebook correspondence, including sexually explicit messages. Even two years later, he said, “it’s a very traumatic story.”
The Associated Press found that Lobkov was targeted by the hacking group known as Fancy Bear in March 2015, nine months before his messages were leaked. He was one of at least 200 journalists, publishers and bloggers targeted by the group as early as mid-2014 and as recently as a few months ago.
WATCH: Russian hacker accused of $4B bitcoin fraud to be extradited to U.S.

The AP identified journalists as the third-largest group on a hacking hit list obtained from cybersecurity firm Secureworks, after diplomatic personnel and U.S. Democrats. About 50 of the journalists worked at The New York Times. Another 50 were either foreign correspondents based in Moscow or Russian reporters like Lobkov who worked for independent news outlets. Others were prominent media figures in Ukraine, Moldova, the Baltics or Washington.
The list of journalists provides new evidence for the U.S. intelligence community’s conclusion that Fancy Bear acted on behalf of the Russian government when it intervened in the U.S. presidential election. Spy agencies say the hackers were working to help Republican Donald Trump. The Russian government has denied interfering in the American election.
Previous AP reporting has shown how Fancy Bear — which Secureworks nicknamed Iron Twilight — used phishing emails to try to compromise Russian opposition leaders, Ukrainian politicians and U.S. intelligence figures, along with Hillary Clinton campaign chairman John Podesta and more than 130 other Democrats.
Lobkov, 50, said he saw hacks like the one that turned his day upside-down in December 2015 as dress rehearsals for the email leaks that struck the Democrats in the United States the following year.
“I think the hackers in the service of the Fatherland were long getting their training on our lot before venturing outside.”

Get breaking National news
‘Classic KGB tactic’
New Yorker writer Masha Gessen said it was also in 2015 — when Secureworks first detected attempts to break into her Gmail — that she began noticing people who seemed to materialize next to her in public places in New York and speak loudly in Russian into their phones as if trying to be overheard. She said this only happened when she put appointments into the online calendar linked to her Google account.
Gessen, the author of a book about Russian President Vladimir Putin’s rise to power, said she saw the incidents as threats.
“It was really obvious,” she said. “It was a classic KGB intimidation tactic.”
Other U.S.-based journalists targeted include Josh Rogin, a Washington Post columnist, and Shane Harris, who was covering the intelligence community for The Daily Beast in 2015. Harris said he dodged the phishing attempt, forwarding the email to a source in the security industry who told him almost immediately that Fancy Bear was involved.
WATCH: Sources tell CBS news they believe Vladimir Putin approved of Russian hacking of U.S. election

In Russia, the majority of journalists targeted by the hackers worked for independent news outlets like Novaya Gazeta or Vedomosti, though a few — such as Tina Kandelaki and Ksenia Sobchak — are more mainstream. Sobchak has even launched an improbable bid for the Russian presidency.
Investigative reporter Roman Shleynov noted that the Gmail hackers targeted was the one he used while working on the Panama Papers, the expose of international tax avoidance that implicated members of Putin’s inner circle.
Fancy Bear also pursued more than 30 media targets in Ukraine, including many journalists at the Kyiv Post and others who have reported from the front lines of the Russia-backed war in the country’s east.
Nataliya Gumenyuk, co-founder of Ukrainian internet news site Hromadske, said the hackers were hunting for compromising information.
“The idea was to discredit the independent Ukrainian voices,” she said.
The hackers also tried to break into the personal Gmail account of Ellen Barry, The New York Times’ former Moscow bureau chief.
Her newspaper appears to have been a favorite target. Fancy Bear sent phishing emails to roughly 50 of Barry’s colleagues at The Times in late 2014, according to two people familiar with the matter. They spoke on condition of anonymity to discuss confidential data.
The Times confirmed in a brief statement that its employees received the malicious messages, but the newspaper declined to comment further.
Some journalists saw their presence on the hackers’ hit list as vindication. Among them were CNN security analyst Michael Weiss and Brookings Institution visiting fellow Jamie Kirchick, who took the news as a badge of honor.
WATCH: FBI failed to warn U.S. targets as Russian hackers targeted emails

“I’m very proud to hear that,” Kirchick said.
The Committee to Protect Journalists said the wide net cast by Fancy Bear underscores efforts by governments worldwide to use hacking against journalists.
“It’s about gaining access to sources and intimidating those journalists,” said Courtney C. Radsch, the group’s advocacy director.
In Russia, the stakes are particularly high. The committee has counted 38 murders of journalists there since 1992.
Many journalists told the AP they knew they were under threat, explaining that they had added a second layer of password protection to their emails and only chatted over encrypted messaging apps like Telegram, WhatsApp or Signal.
Fancy Bear target Ekaterina Vinokurova, who works for regional media outlet Znak, said she routinely deletes her emails.
“I understand that my accounts may be hacked at any time,” she said in a telephone interview. “I’m ready for them.”
‘I’ve seen what they could do’
It’s not just whom the hackers tried to spy on that points to the Russian government.
It’s when.
Maria Titizian, an Armenian journalist, immediately found significance in the date she was targeted: June 26, 2015.
“It was Electric Yerevan,” she said, referring to protests over rising energy bills that she reported on. The protests that rocked Armenia’s capital that summer were initially seen by some in Moscow as a threat to Russian influence.
Titizian said her outspoken criticism of the Kremlin’s “colonial attitude” toward Armenia could have made her a target.
WATCH: Russia probe investigator slams Twitter over lack of information into interference

Eliot Higgins, whose open source journalism site Bellingcat repeatedly crops up on the target list, said the phishing attempts seemed to begin “once we started really making strong statements about MH17,” the Malaysian airliner shot out of the sky over eastern Ukraine in 2014, killing 298 people. Bellingcat played a key role in marshaling the evidence that the plane was destroyed by a Russian missile — Moscow’s denials notwithstanding.
The clearest timing for a hacking attempt may have been that of Adrian Chen.
On June 2, 2015, Chen published a prescient expose of the Internet Research Agency, the Russian “troll factory” that won fresh infamy in October over revelations that it had manufactured make-believe Americans to pollute social media with toxic rhetoric.
Eight days after Chen published his big story, Fancy Bear tried to break into his account.
Chen, who has regularly written about the darker recesses of the internet, said having a lifetime of private messages exposed to the internet could be devastating.
“I’ve covered a lot of these leaks,” he said. “I’ve seen what they could do.”
Donn reported from Plymouth, Massachusetts. Vasilyeva reported from Moscow. Kate de Pury in Moscow contributed.







Comments
Want to discuss? Please read our Commenting Policy first.