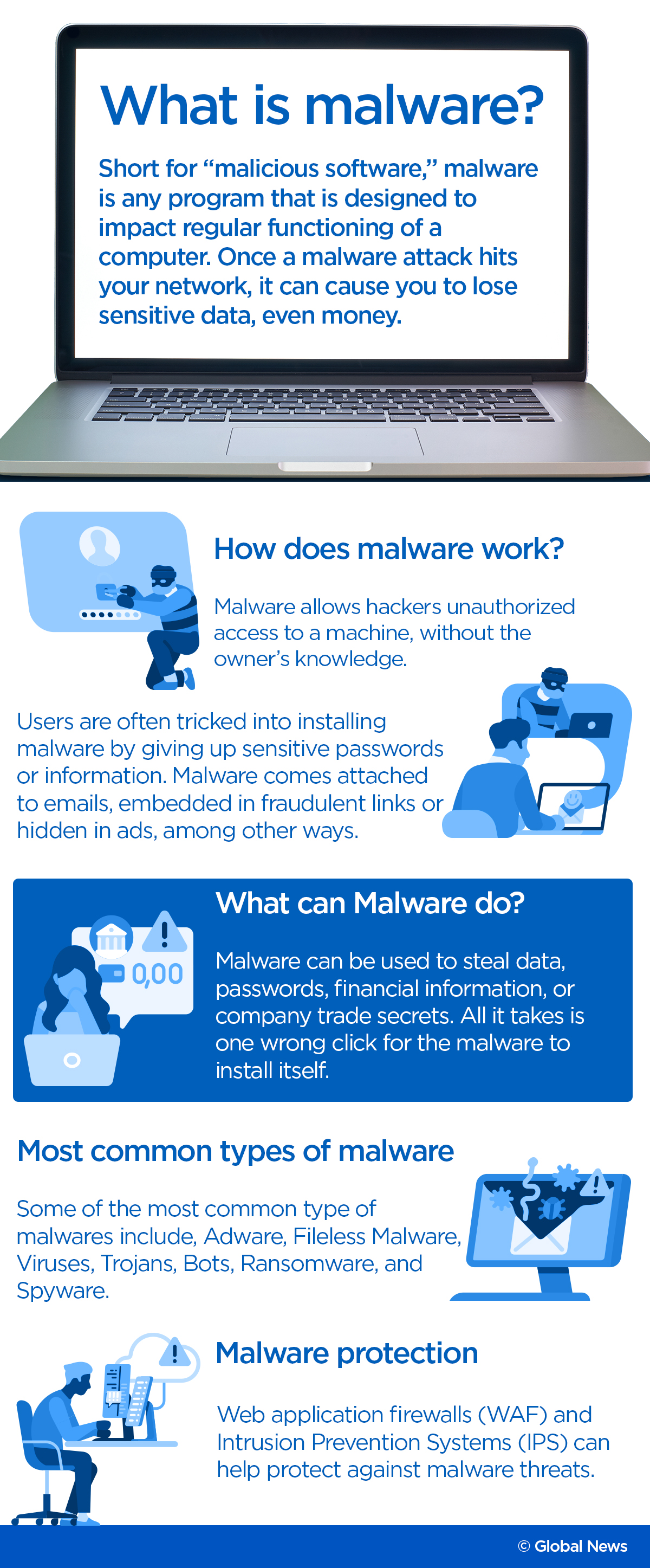
The Canadian Centre for Cyber Security sent out a public alert Friday saying that the centre has become aware of a new disruptive malware, named HermeticWiper, targeting Ukrainian organizations.

The alert, which is being released to raise awareness, comes after the malware, or malicious software, was found circulating in Ukraine on Wednesday.
Reuters reported that the malware has hit hundreds of computers, according to researchers at the Ukrainian cybersecurity firm ESET. Suspicion fell on Russia, which has repeatedly been accused of hacks against Ukraine and other countries. The victims included government agencies and a financial institution, but no further details were provided.
According to the Canadian cybersecurity centre, HermeticWiper “abuses a benign driver to corrupt the Master Boot Record (MBR) of every physical drive and each drive partition to make the victim system inoperable after machine shutdown.”
HermeticWiper “also modifies several registry keys to disable system crash dumps.”
In a nutshell, says ethical hacker and CEO of Cyology Terry Cutler, this new malware basically goes on to “wipe all data of a government agency or company,” making it unrecoverable.
Difference between HermaticWiper and Ransomware
Ransomeware is a commonly known type of malware. What makes HermeticWiper different from usual malware is the way it affects and uses data.
According to Cutler, when ransomware gets inside a computer, it gains access to usernames and passwords and digs its way through the system.
“It tries to get a foothold, and once it gets to what’s called domain administrative credentials … the computers get locked up and their data becomes completely unusable and scrambled until you pay a ransom,” Cutler explained in an interview with Global News.
The HermaticWiper, on the other hand, “goes out and instead of doing the ransomware thing where it’s locking up data, it’s actually wiping the whole place clean, which is far more troublesome to get back,” said Cutler.

Russia’s cyberwarfare

Get daily National news
In a document prepared by the Congressional Research Service (CRS) in early February of this year, the CRS explained that Russia maintains a number of cyber units that “conduct disinformation, propaganda, espionage and destructive cyberattacks globally.”
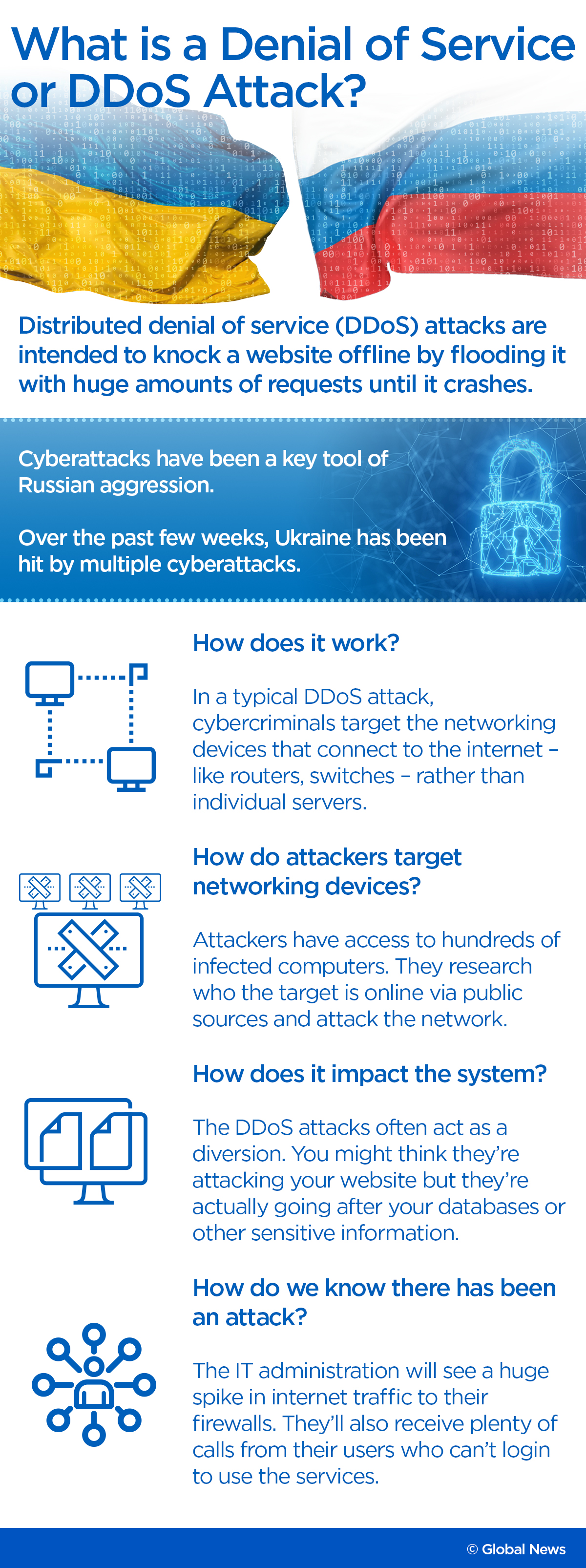
The CRS said that according to government reports, Russia’s initial cyber operations primarily consisted of Distributed Denial of Service (DDoS) attacks and often relied on the recruitment of criminal and civilian hackers.
Cutler explained that a DDoS attack is a cyberattack aimed to disrupt the normal traffic of a targeted server, service or network by overwhelming the target or its surrounding infrastructure with a flood of Internet traffic.
READ MORE: Ukraine says ‘full-scale invasion’ by Russia underway as Putin orders military attack
He said that DDoS often acts as a diversion.
“You’ll think they’re attacking your website but in fact, they’re going after your databases or other sensitive information,” Cutler said.
When it does happen, he said the IT administration will see a huge spike in internet traffic to their firewalls. They’ll also get a ton of calls from their users who can’t log in to use the services as well.
Cutler said Russia’s cyberwarfare units have the “playbooks to stay undetected as long as possible.”
“They try to hack their way into what’s called critical infrastructure. They want to get into your electricity grid, your water supply, your phone, your internet providers…If it ever came down to a World War Three, it might not be fought with bombs anymore. It’s going to be fought with cyberattacks,” Cutler said.
Ukraine has been subject to a steady barrage of Russian aggression in cyberspace since 2014, when Russia annexed the Crimean Peninsula and backed separatists in eastern Ukraine.
In 2007, Estonia was also the target of a large-scale cyberattack, which most observers blamed on Russia. Estonian targets ranged from online banking and media outlets to government websites and email services.
Russia again employed DDoS attacks during its 2008 war with Georgia. Although Russia denied responsibility, Georgia was the victim of a large-scale cyberattack that corresponded with Russian military actions.

How to stop this new malware
The HermiticWiper is only working because it’s new. If it was old, then existing countermeasures would have found and it would have been stopped, says Eric Parent, CEO and founder of EVA technologies who specializes in cybersecurity and cyber-terrorism.
Parent says once HermeticWiper “detonates and breaks things,” there will be different people and entities, like antivirus and emergency response companies, studying it.
“The good part is that (after we figure out how it does its thing) we can see how to protect ourselves against it,” said Parent. “The bad part is that all the bad people can also look it and figure out how it works too.”
READ MORE: Russian cyber threat compounds tensions in Ukraine as invasion worries grow
He said in time criminals can figure out how HermeticWiper works and use it on somebody else.
In the meantime, as Russia continues its invasion of Ukraine, Parent says he expects to see more cyberattacks taking place in the coming days and weeks, even in Canada, and they’ll be a little different.
“We’ve always had some … but we’re just going to have a little bit more … and there’s going to be a little bit more targeted efforts,” said Parent.

Are Canadian businesses at risk?
A cybersecurity expert says Canadian businesses are at risk of being targeted for online attacks if Russia chooses to retaliate against government sanctions.
Karim Hijazi, founder and CEO of Texas-based cyberintelligence firm Prevailion, says that Canadian companies could be victims of bad actors trying to compromise critical infrastructure and government entities.
He says this could be the likely approach because government, critical infrastructure and the private sector are so intertwined and subject to easy access.
Hijazi also says that the damaging malware that Russia could activate is already in Canada.
READ MORE: Explosions rock Kyiv as Ukraine capital prepares for Russian assault
A spokesperson from the Communications Security Establishment (CSE) said confirmed to The Canadian Press that the federal government agency is watching for cyber threats directed at the financial, energy and telecommunications sectors.
The CSE encourages all of Canada’s critical infrastructure sectors to monitor increased cyber threat activity.
Parent said Russia would retaliate against the countries that are placing sanctions on it through cyberattacks because “it’s too easy to do that.”
“If they find something they can break, that’s on Canadian or American soil, they’re going to do it.”
— with files from The Canadian Press, the Associated Press and Reuters








Comments
Want to discuss? Please read our Commenting Policy first.