A cybersecurity incident that left Elgin County’s website and email services offline through the month of April resulted in thousands of county files, some containing highly sensitive personal information, being posted to the dark web, Elgin’s chief administrative officer confirmed on Monday.

Officials in the county south of London, Ont., have kept mum about the incident over the last several weeks, but now say that roughly 26,000 files and the information of about 300 people were compromised after an “unauthorized third party” gained access to its network.
Highly sensitive data pertaining to 33 people, including social insurance numbers, health card numbers and financial information, was also among the data posted, said Julie Gonyou, Elgin’s CAO, in an interview with Global News.
“We are providing 12 months of credit monitoring and identity theft protection to those 33 individuals whose sensitive information was compromised,” Gonyou said on Monday.
For the more than 260 others who were impacted, the compromised information included data not necessarily of high value to cybercriminals, but which could present more of a reputational risk, like performance appraisals and termination letters, she said.
“Those impacted were really current and former staff of the County of Elgin, as well as current and former residents of our long-term care home facilities. In the long-term care home facilities, there were five individuals impacted,” Gonyou said. The county operates three long-term care facilities, including Bobier Villa, Elgin Mayor and Terrace Lodge.
“We took immediate action to notify those individuals … All notifications went out on Friday.”
County officials first confirmed that a “cyber security incident” had occurred in a memo that was circulated to staff on March 31 and obtained by the London Free Press.
In the memo, Gonyou wrote that a large amount of spam containing malicious attachments or links was being sent to staff members and that an external consultant had been hired to investigate the incident and monitor for data breaches.
On Monday, Gonyou said that after learning of the unauthorized network access, the network was shut down immediately on April 1 to mitigate further damage — a shut down which would last until April 27, impacting the county’s website and email services.
On May 3, Elgin officials were alerted by their cybersecurity consultant that information had been dumped on the dark web, she said.
“It was 26,000 files, some of which were not active. Really, it was a file directory that was posted. We manually went through and assessed each of the 26,000 files to review against a set of criteria,” Gonyou said.
“I would say this was a very, very small percentage of the total file volume that we host at the county. And it was kind of a sampling across multiple different servers and different files.”
There was no “rhyme or reason” as to the service areas that were impacted by the breach, Gonyou says, noting the county provides about 25 different services. “It’s hard to discern whether certain areas were impacted more than others.”
Global News first reported in late April that a cybersecurity expert observed that data purporting to belong to the county had been posted to the dark web portal of the notorious Russian ransomware group Conti.
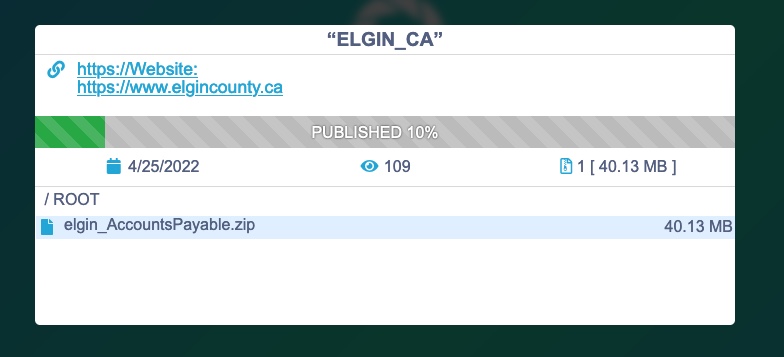
The data purportedly uploaded included at least one 40 megabyte ZIP file labelled “elgin_AccountsPayable.” Global News could not independently verify the authenticity of the Conti listing or the data allegedly posted as it appeared to have already been removed by the following day.

Get daily National news
What caused the cybersecurity incident remains under investigation, but Gonyou says the incident was not, to their knowledge, a ransomware attack.
“We shut down our network, which I think is very distinct from a ransomware attack, where I think under those circumstances the cybercriminals or threat actors shut down your system or hold your information for ransom,” she said. The county did not pay out a ransom, and its systems were brought back online on April 27, she said.
One cyber threat expert, however, says it all depends on your definition of ransomware.
“Ransomware has evolved in the last couple of years,” said Brett Callow, a Vancouver Island-based threat analyst with cybersecurity firm Emsisoft.
“In the past, they used to simply lock up their targets’ networks. They still do that sometimes, but they also steal a copy of the data and use that as additional leverage to extort payment. Sometimes they skip the encryption process completely and simply steal the data.”
Asked whether Conti was believed to have been involved in the incident, or whether contact had been made with the group either by the county or its cybersecurity consultant, Gonyou declined to comment citing an ongoing investigation by Ontario Provincial Police with which the county is cooperating.
Gonyou said Monday that she wasn’t aware whether any of the compromised information had been taken offline.
“I think once it’s posted that … presents a risk regardless,” she said.
Since publishing the initial Conti story in late April, Global News has learned that purported Elgin data has also been posted to the dark web portal of another ransomware group. Global News is not identifying the group as the data was still live as of Monday afternoon.
That data dump, measuring about 50 gigabytes, also contains an “elgin_AccountsPayable” folder, along with directories labelled “Engineering,” “elgin_data” and “elgin_hr.”
“Thank you for that information. I’ll follow up, but I have no further comment,” Gonyou said when told of the other data dump. Gonyou also declined to say if the county had had any contact with any ransomware group, citing the OPP investigation.

Asked whether it was unusual to see data posted to the portals of two different ransomware groups, Callow explained that most ransomware groups work on a ransomware-as-a-service basis.
“You have the team who create the ransomware, and they, in effect, rent it to other people who use it in their attacks” — affiliates — “and they all split the proceeds between them,” he said.
“One possibility here is that an affiliate carried out the attack using Conti’s ransomware, that Conti gave up on it, and so the affiliates took it to another ransomware group to try and extort money.”
According to the Canadian Centre for Cyber Security, Conti is considered “one of the most sophisticated ransomware groups in operation,” and frequently targets hospitals, governments, medical networks and other critical services.
Speaking with Global News last month, Callow said it was unlikely that Elgin was targeted for any particular reason, and that an overwhelming majority of attacks are done at random via malicious links in phishing emails or unpatched vulnerabilities on internet-facing networks.
In the wake of the cybersecurity incident, Gonyou said the county had implemented additional safeguards and protections for its IT network.
“We are conducting regular health systems checks and enhancing our staff training across the corporation. As well our work with our external cybersecurity team is ongoing, so we’ll continue to investigate the matter,” she said.
“We look forward to receiving any recommendations from our consultants as well.”
With the prevalence of cyberattacks increasing across businesses large and small, Gonyou says other organizations should learn from Elgin’s case and be hyper-vigilant about cyber threats.
“Elgin County did have robust systems in place, so the threat actors or perpetrators, they’re using very sophisticated means by which to infiltrate IT systems and networks,” she said.
According to the Canadian Centre for Cyber Security (CCCS), ransomware is the most common cyber threat that Canadians face.
“Ransomware is not a new problem. Observed as early as 1989, over the past 15 years ransomware has become one of the most popular types of cybercrime,” a 2021 cyber threat bulletin from CCCS reads.
The bulletin notes that ransomware-as-a-service operations have helped increase the impact and scale of ransomware attacks over the last few years. According to the agency, global ransomware attacks increased 151 per cent in the first half of 2021 compared to the same time in 2020.
“The Cyber Centre has knowledge of 235 ransomware incidents against Canadian victims from 1 January to 16 November 2021. More than half of these victims were critical infrastructure providers,” the bulletin reads, adding that most attacks go unreported, and victims can be hit multiple times.
“Despite a temporary lull following international action, we assess that ransomware will continue to pose a threat to the national security and economic prosperity of Canada and its allies in 2022 as it remains a profitable activity for cybercriminals.”
















Comments
Comments closed.
Due to the sensitive and/or legal subject matter of some of the content on globalnews.ca, we reserve the ability to disable comments from time to time.
Please see our Commenting Policy for more.