WATCH ABOVE: 16×9’s “You’ve Been Hacked”

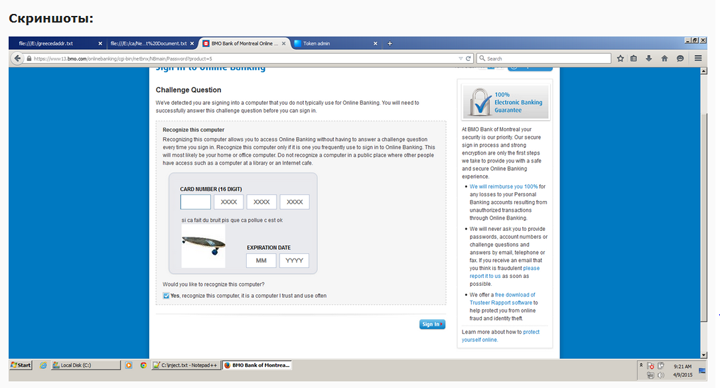
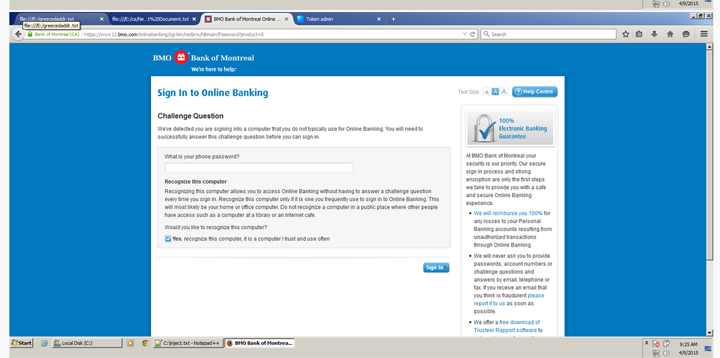
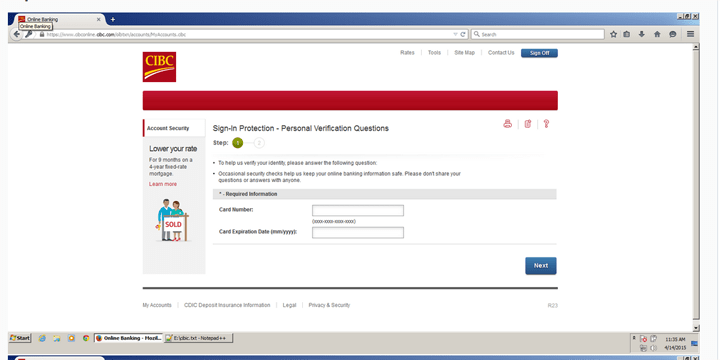
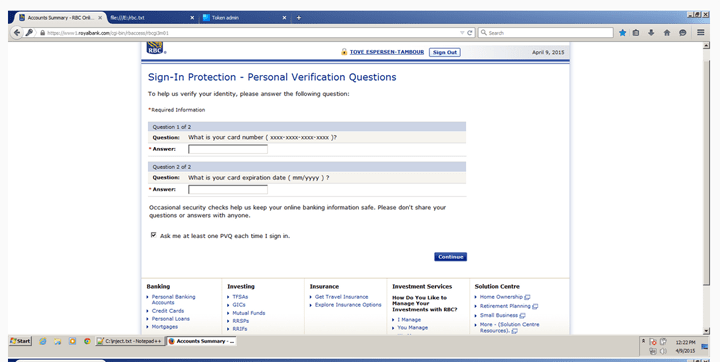
Underground forums selling fake Canadian banking websites could be putting your savings at risk. A 16×9 investigation has uncovered fake templates, for major Canadian banks, advertised in Russian.
BELOW: Fake Canadian banking websites advertised in Russian on an underground forum
READ MORE: Cybersecurity firm says a ring of hackers has stolen $1B from banks
Fraudulent banking websites, like these, are commonly used as part of banking trojan attacks, which are designed to steal money from your account. Most often the criminals behind these attacks live in Russian-speaking countries, where the lack of extradition treaties makes it easier for hackers to operate.
The banking trojans target countries indiscriminately. Tens of thousands of Canadians were targeted by banking attacks in 2014, with infections continuing well into 2015.
“It’s a horrible feeling to know that it’s gone,” says Lee Hanson of the Atlanta-based Hanson Group, which lost $160,000 to a banking trojan.
“We’re not a large corporation. We employ a decent amount of people, but to lose $160,000 … what do you do?”
Hanson was one of hundreds of thousands of people and companies that were hit as part of one of the most sophisticated banking attacks ever, called GameOver Zeus. GameOver Zeus affected 226 countries between 2011 and 2014, infecting well over a million computers.
So complex was the design of GameOver Zeus, that when the FBI was tasked with stopping the spread of infections they weren’t sure they could.
“To be honest with you, our initial reaction was we can’t take this down,” Supervisory Special Agent Tom Grasso said.
The cyber criminals behind GameOver Zeus were in command of hundreds of thousands computers around the world, called a botnet. But instead of a traditional web of infected computers, which receives orders from one central command and control server, the computers infected with GameOver Zeus communicated amongst themselves.
READ MORE: Keeping your wallet safe from the security-ridden online jungle
This time, the enemy wasn’t a snake where you could simply cut off its head and neutralize the threat, says SSA Grasso.
“There were many heads. It was a Medusa.”
BELOW: How GameOver Zeus differs from other banking trojans
GameOver Zeus became a global outbreak. A single infected computer caused damages ranging from $10,000 to $6.9 million, taken from a bank in Florida.
Most often, the infection begins with a simple email.
“You’ll receive an email where there’s something you need to click on,” Andy Chandler, with the Dutch cybersecurity firm Fox-IT, said.
“So it might tell you, you have an outstanding pay invoice and therefore you, as the lady in the accounts department, will click on that to see what it’s for and how much it’s for…. And you’re infected.”
The cybercriminal is now in charge of your computer.
WATCH ABOVE: What can you do to protect yourself from an online bank attack?
Then, when you log in to your bank account, the hacker sees exactly what you do – and can steal your money.
READ MORE: Hackers are using the Starbucks app to skim bank accounts, credit cards
“They’ll serve up a screen, which overlays what you currently see, which is basically the same banking details and everything,” Chandler explained.
“The criminal that you’ve authenticated, who’s now inside your account, is setting up a new sender account, somewhere where they can send your money.”
It took the FBI and a team of private security firms until June 2014 to finally disable the GameOver Zeus banking trojan. By that time, more than a million computers around the world had been infected.
You can watch the complete 16×9 investigation, “You’ve Been Hacked”, Saturday Nov. 14 at 7pm – on Global.













Comments