Hackers and spammers have developed a new way to infect computers that only requires a potential victim to hover over a hyperlink within a PowerPoint presentation slide, no click required.

The folks at Trend Micro, an IT security solutions company, recently discovered a new method hackers can use to deliver malware to a computer without requiring a user to click on a link or download a sketchy file from phishing emails.
According to the IT company, the Trojan activates when a potential victim hovers their computer mouse over a text link or image within the fake PowerPoint slide that is usually delivered via spam email. The Trojan targets banking information and web browser information and remote access to the infected computer.
READ MORE: French experts find way to save WannaCry-infected files without ransom
As Bleeping Computer points out, the single PowerPoint slide is delivered as an attachment on phishing scam emails with subject lines to the likes of “RE:Purchase orders #69812″ or “Fwd:Confirmation,” suggesting someone had made an online purchase.
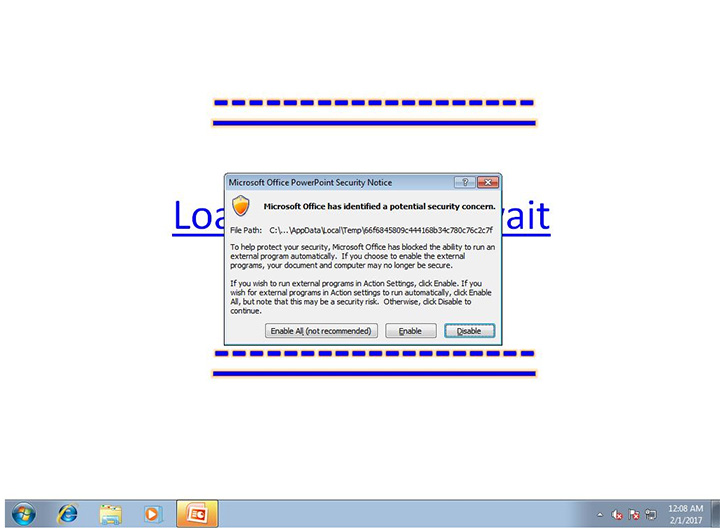
Once a user hovers over the link, the code will then prompt Microsoft PowerShell to run the malicious code. Depending on the version of Microsoft Office the potential victim is using, PowerShell may automatically allow the infected script to run or be flagged as a “potential security risk” before the script can be executed.
As Trend Micro points out, Microsoft “disables the content of suspicious files by default—via Protected View (in PowerPoint) for later versions of Office.”
“Users are recommended to use Protected View, which Microsoft enables by default, especially to documents downloaded from possibly unsafe locations,” the security company said in a blog post.
READ MORE: Ransomware like WannaCry is an ‘escalating threat,’ says Europol Director
“Protected View provides a way for users to read the content of an unknown or suspicious file while significantly reducing chances of infection.”
According to Trend Micro, the delivery method is new but the malware in the PowerPoint scam has been around since at least 2012. In 2015, the malware was used in France, hidden in messages that appeared to be from the ministry of justice.
The security company also noted that the PowerPoint email campaign has been small so far and only reported in Europe and the Middle East, noting that it could be a “dry run” for future “campaigns.”







Comments